Lesson1:
The von Neumann architecture:
The von Neumann architecture involves a Central processing unit,Random Access Memory, and Input Output circuitry.
图很重要!
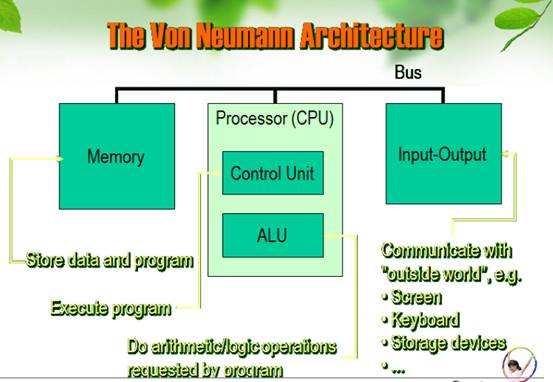
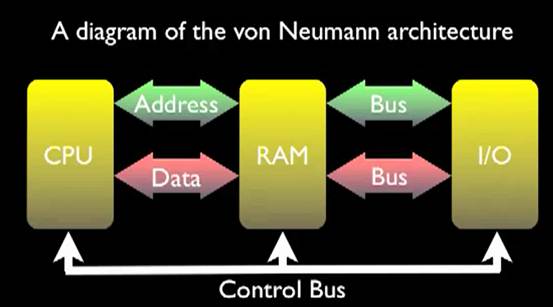
CPU is central processing unit. Include The Control Unit. The Registers. The ALU. The Prefetch Unit. The Decode Unit. The Bus Unit.(Address bus,Data bus)The Data Cache. The Instruction Cache.
The component of CPU are Silicon,Wafer,Semiconductor,Polysilicon,Photoresist,Ingot,Etch, Solvent.
Computer types:
Supercomputer: the most powerful type of mainframe
Mainframe: large, very powerful, multi-user, multi-tasking
Minicomputer: smaller than a mainframe, powerful, multi-user, multi-tasking
Personal computer: single user
Desktop computer: suitable size for sitting on an office desk
Workstation: most powerful type of desktop, used for graphic design
Portable: can be carried around, can operate with batteries
Laptop: large portable, can be rested on user’s lap
Notebook: size of a sheet of notebook paper
Handheld: can be held in one hand
Pen-based: main input device is an electronic pen
PAD: personal digital assistant, has functions such as task list, diary, address book
How cache works?简答
1.CPU requests new data.
2.Data is not found in cache. Cache requests data from hard disk.
3.Cache reads data from multiple sector on disk, including data adjacent to that requested.
4.Cache replaces old data with new data.
5.Cache supplies CPU with requested data.
Terms:
Write-back cache:回写式高速缓存
Write-through cache:直写式高速缓存
Cache hit:缓存命中
SD RAM:同步RAM
Arithmetic logical unit:算数逻辑单元
bus: a set of conductors that carry signals between different parts of a computer.
microprocessor 微处理器: the main electronic chip in a computer. It can be thought of as the 'brain' of the computer because it does the main processing and controls the other parts of the computer. It is sometimes called the CPU.
Lesson2
Term:部分可能为名词解释
API:Application program interface 应用程序接口
Maskable interrupt: 可屏蔽中断
Non-maskable interrupt: 非屏蔽性中断
Program: the set of instructions that is actually running.
(进程:加载到内存的一组代码+分配的资源)
thread: The thread is made up of an individual instruction set and the data that must be worked on by the CPU. 线程
Cooprative multitasking: 协调式多重任务处理。由程序自己控制资源使用时间
Preemptive multitasking: 抢占式多重任务处理。由OS控制资源使用时间
Kernel: In computing, the kernel is the main component of most computer operating system; it is a bridge between applications and the actual data processing done at the hardware level.
Types of Operating Systems:(important)简答
1.Real-time operating system(RTOS)
(?used to control machinery, scientific instruments and industrial systems.
?has very little user-interface capability, and no end-user utilities)
?WinCE、VxWorks
2.Single-user, single-task
(?designed to manage the computer so that one user can effectively do one thing at a time
?e.g. The Palm OS for Palm handheld computers.)
3.Single-user, multi-tasking
(?Microsoft's Windows and Apple's Mac OS platforms are both examples of operating systems that will let a single user have several programs in operation at the same time.)
4.Multi-user
(? allows many different users to take advantage of the computer's resources simultaneously
?e.g. Unix, VMS and MVS.)
Operating System Function:简答
Arbitration
?It manages the hardware and software resources of the system. managing the hardware and software resources, is very important, as various programs and input methods compete for the attention of the central processing unit (CPU) and demand memory, storage and input/output (I/O) bandwidth for their own purposes.
Abstraction
It provides a consistent application interface. It provides a stable, consistent way for applications to deal with the hardware without having to know all the details of the hardware.
The relationship between thread and process :
A process is a program in memory whereas the thread is in CPU. A process can create several threads and those thread shares the resources of the process.
Operating system architecture:
?Process management
?Memory management
?Device Management
名词解释

Translation
?Some examples of the functionality that individual processes provide include displaying data onscreen, spooling print jobs, and saving data to temporary files.
举一些个体进程提供功能的例子,包括将数据显示在屏幕上,后台打印作业,将数据保存到临时文件上
?Users would interact with their computations, one at a time on the machine and at the lowest machine level, by manually examining and setting machine registers, stepping through instructions, and looking at contents of memory locations.
用户与计算机互动,一次一个并以最低的机器配置,通过手动检查和设定寄存器,通过加强指导,等待存储单元的内容。
?In these early years of computing(信息处理), programming aids were either nonexistent or minimal; the most advanced installations featured assemblers(汇编程序) to liberate the user from the lowest-level machine language programming, and a few rudimentary(基本的) library routines(程序) to handle the most tedious(乏味的) and repetitive(重复的) tasks.
?This trend can be seen today in the evolution of PCs, with inexpensive hardware being improved sufficiently to allow, in turn, improved characteristics.
在这些早年信息处理时期,编程辅助工具要么不存在或很少;最先进的设备功能的汇编程序为了将用户从最低级的机器编程语言,和一些基本的库程序来处理乏味的和重复的任务中解放出来。
今天可以从电脑的发展趋势中看出,即廉价的硬件被充分提高,反过来以允许改进数据特性。
Lesson 3:
Terms:
DSPs (Digital Signal Processors) 数字信号处理器
IDE (Integrated Development Environment) 集成开发环境
RISC (Reduced instruction set computers) 精简指令集计算机
TCP/IP (Transmission Control Protocol/Internet Protocol) 传输控制协议/网际协议
Assembler 汇编程序、汇编器
Microcontroller:简答
A microcontroller is a computer. Microcontrollers are used in automatically controlled products and devices.
containing a processor core, memory, and programmable input/output peripherals.
Microcontrollers are "embedded" inside some other device (often a consumer product) so that they can control the features or actions of the product.
Microcontrollers are dedicated to one task and run one specific program. The program is stored in ROM (read-only memory) and generally does not change.
Microcontrollers are often low-power devices.
(A desktop computer might consume 50 watts of electricity.
A battery-operated microcontroller might consume 50 milli-watts.)
A microcontroller has a dedicated input device and often (but not always) has a small LED or LCD display for output.
A microcontroller is often small and low cost.
A microcontroller is often,but not always,ruggedized in some way.
The differences between microcontroller and PC:(important)简答
Microcontroller is typically dedicated to a single task.
PC is typically performs a number of tasks or runs a variety of programs simultaneously.
Similarities: both have1.cpu
2.memory
3.system clock
4.peripherals
Types of embedded system:简答
1.Small scale embedded systems(Battery operated)
Small scale embedded systems (a single 8-bit or 16-bit microcontroller, battery operated, have little hardware and software complexities and involve board-level design, main programming tool is C)
2.Medium scale embedded systems
Medium scale embedded systems (a single or few 16-bit or 32-bit microcontroller or DSPs or RISCs, have both hardware and software complexities)
3.Sophisticated embedded systems
Sophisticated embedded systems (have enormous hardware and software complexities and may need scalable processors or configurable processors and programmable logic arrays)
Types of interrupts:
Maskable interrupt 可屏蔽性中断
Non-maskable interrupt: 不可屏蔽性中断
Lesson 4:
Terms:
Frequency of items频繁项集
Support: 支持度
Confidence: 置信度
Association analysis: 关联分析
Classification: 分类分析
Training set: 训练集
Relational database: 关系数据库
Data warehouse: 数据仓库
Transaction database: 交易数据库
Clustering: 聚集分析
Outlier analysis: 离群分析
What the Data Mining is?
Data Mining, also popularly known as Knowledge Discovery in Databases (KDD), refers to the nontrivial extraction of implicit, previously unknown and potentially useful information from data in databases.
While data mining and knowledge discovery in databases (or KDD) are frequently treated as synonyms, data mining is actually part of the knowledge discovery process.
The process of Data Mining:简答
Data cleaning (data cleansing)
Remove: noise data irrelevant data
Data integration
Combine: heterogeneous and multi-sources
Data selection
Retrieve: relevant data
Data transformation(data consolidation)
Transform: forms appropriate
Data mining
Extract: patterns potentially useful
Pattern evaluation
Identify: patterns representing knowledge
Knowledge representation
Visualization techniques
Two types of data mining tasks:
descriptive data mining tasks
predictive data mining tasks
DM functionalities and knowledge discovered:
Characterization
Discrimination
Association analysis
Classification
Prediction
Clustering
Outlier analysis
Evolution and deviation analysis
What kind of information are we collecting:
Business transactions
Scientific data
Medical and personal data
Surveillance video and pictures
Satellite sensing
Games
Digital media
CAD and Software engineering data
Virtual Worlds
Text reports and memos(e-mail messages)
The world wide web repositories
Branch of DM:
Data characterization is a summarization of general features of objects in a target class, and produces what is called characteristic rules.
Data discrimination produces what are called discriminant rules and is basically the comparison of the general features of objects between two classes referred to as the target class and the contrasting class.
Association analysis is the discovery of what are commonly called association rules. It studies the frequency of items occurring together in transactional databases.
Threshold:
Support identifies the frequent item sets
Confidence which is the conditional probability than an item appears in a transaction when another item appears.
Association analysis is commonly used for market basket analysis.
Classification analysis is the organization of data in given classes. Also known as supervised classification, the classification uses given class labels to order the objects in the data collection.
Classification approaches normally use a training set where all objects are already associated with known class labels.
The classification algorithm learns from the training set and builds a model( classify new objects).
Prediction has attracted considerable attention given the potential implications of successful forecasting in a business context.
There are two major types of predictions:
predict some unavailable data values or pending trends
predict a class label for some data→ classification.
The major idea is to use a large number of past values to consider probable future values.
Clustering is the organization of data in classes. class labels are unknown and it is up to the clustering algorithm to discover acceptable classes.
unsupervised classification
Clustering approaches:
maximizing the similarity between objects in a same class (intra-class similarity
minimizing the similarity between objects of different classes(inter-class similarity).
Outliers are data elements that cannot be grouped in a given class or cluster. Also known as exceptions or surprises, they are often very important to identify.
While outliers can be considered noise and discarded in some applications, they can reveal important knowledge in other domains, and thus can be very significant and their analysis valuable.
Evolution and deviation analysis pertain to the study of time related data that changes in time.
Evolution analysis models evolutionary trends in data, which consent to characterizing, comparing, classifying or clustering of time related data.
Deviation analysis considers differences between measured values and expected values, and attempts to find the cause of the deviations from the anticipated values.
Lesson5:
Terms:
Scam (网络)诈骗
Spam 垃圾邮件
Fraud 诈骗
Antivirus 防病毒
Spyware 间谍软件,后门程式
Trojans 特洛伊木马,木马
Adware 广告软件
Backup 备份
Computer Virus & Worms 病毒、蠕虫
Phishing 钓鱼(网站)
Malware 恶意软件
Steganography 隐写术
Information Hiding 信息隐藏
Covert Channel 隐蔽通信
Watermarking 水印
Embedded 嵌入
Something to be hidden in something else.
Stego 隐写信息
The output of the hiding process; something that has the embedded message hidden in it.
Cover 载体
An input with an “original” form of the stego-message.
Stego-key or simply key 密钥
Additional secret data that may be needed in the hiding process.
Embedding 嵌入
The process of hiding the embedded message is called embedding.
Extracting 提取
Getting the embedded message out of the stego-message again is called extracting.
IDS Intrusion Detection System 入侵检测系统
IPS Intrusion Prevention System 入侵防御系统
APT Advanced persistent threat 进阶持续性渗透攻击
UTM Unified Threat Management 统一威胁管理
NGFW Next Generation Firewall 下一代防火墙
VPN Virtual Private Network 虚拟专用网
SSL Secure Sockets Layer 安全套接层
Dos attack denial-of-service attack 拒绝服务攻击
DPI Deep Packet Inspection 深度包检测
Translation:
Steganography refers to methods that are used to transmit the embedded message without an observer being aware that there is an embedded message in the cover message.
隐写术指的是用于发送嵌入消息而不观察者意识到有在消息嵌入在载体信息的方法。
The similar field of watermarking is to embed a "watermark" for the purpose of authentication, a crucial step for copyright protection and tamper proofing.
水印的相似领域是为了嵌入一个“水印”以达到认证的目的,是版权保护和防止篡改的关键一步。
Three different aspects in information-hiding systems contend with each other: capacity, security, and robustness. Capacity refers to the amount of information that can be hidden in the cover medium, security to an eavesdropper’s inability to detect hidden information, and robustness to the amount of modification the stego medium can withstand before an adversary can destroy hidden information.
在信息隐藏系统三个不同方面互相制约:容量,安全性和稳健性。容量指的信息可以隐藏在载体介质的大小,安全性是指窃听无法检测到的隐藏信息,稳健性达到可以更改隐写信息媒介时可以在对方破坏隐藏信息之前反抗
Network security:
Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources.
What is data security?
Data security is the practice of keeping data protected from corruption and unauthorized access.
The focus behind data security is to ensure privacy while protecting personal or corporate data.
There are a number of options for locking down your data from software solutions to hardware mechanisms.
Inside network security:
Firewall, FW
Stateless firewall
Stateful firewall
Endpoint security
Intrusion prevention system, IPS
Denial of service
Advance persistent threat, APT
Virtual private network, VPN
SSL VPN
Branch office VPN
Wireless networking
Next generation firewall, NGFW
Unified Threat Management, UTM
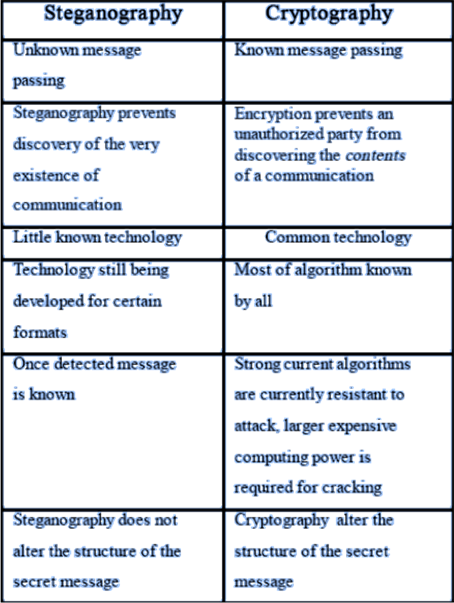
The two way to protect data security is steganography and cryptography.
Steganography is the art and science of writing hidden messages in such a way that no one apart from the intended recipient knows of existence of the message.
Steganalysis
Steganalysis concentrates on the art and science of finding and or destroying secret messages that have been produced using any of the various steganographic techniques.
Steganographic technologies are a very important part of the future of Internet security and privacy on open systems such as the Internet.
The way to attack:
Stego only attack - only the stego object is available for analysis.
Known cover attack - the original cover object and the stego object are available for analysis.
Known message attack - the hidden message is available to compare with the stego-object.
Chosen stego attack - the stego tool (algorithm) and stego-object are available for analysis.
Chosen message attack - takes a chosen message and generates a stego object for future analysis.
Known stego attack - the stego tool (algorithm), the cover message and the stego-objects are available for analysis.
Cryptography is derived from the Greek words
cryptos, meaning hidden
graphien, meaning to write
Cryptography is the art and science of transforming data into a sequence of bits that appears as random and meaningless to a side observer or attacker.
It scrambles a message so it cannot be understood.
Cryptanalysis encompasses all of the techniques to recover the plaintext and/or key from the ciphertext.
Ps:
Terms 是我认为可能会考到的名词解释或者翻译中可能会出现的单词。
这是本人猜测的需要复习的内容。这次添加的内容大多由罗声悦赞助~~前两个图片要注意下可能有关简答题。。总结的可能不是很全面,因为我也没上过课。。。各单元单词部分除了六单元其他我没有罗列,大家在书本上背诵。在课本上标题是Part one operating system 和what is microcontroller这两篇文章我没有打出来。但是是重点,估计会考翻译吧。需要着重看。大家考试加油~
