1.1 实验任务
在路由器组上配置VPN
1.2 实验环境和网络拓扑
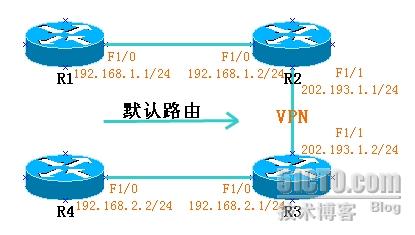
1.3 完成标准
(1) 按照拓扑配置路由,保证网络的连通性
(2) 在R2和R3上配置VPN,并检查VPN配置
2.详细操作步骤
Step 1: 配置接口、路由并检查网络连通性
(1) 配置各交换机的接口和路由
路由器R1配置如下:
R1(config)#int f1/0
R1(config-if)#ip add 192.168.1.1 255.255.255.0
R1(config-if)#no shut
R1(config-if)#
*Dec 27 16:36:52.115: %LINK-3-UPDOWN: Interface FastEthernet1/0, changed stat
o up
*Dec 27 16:36:53.115: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEth
et1/0, changed state to up
R1(config-if)#exit
R1(config)#ip route 0.0.0.0 0.0.0.0 192.168.1.2
路由器R2配置如下:
R2(config)#int f1/0
R2(config-if)#ip add 192.168.1.2 255.255.255.0
R2(config-if)#no shut
R2(config-if)#
*Dec 27 16:37:12.027: %LINK-3-UPDOWN: Interface FastEthernet1/0, changed stat
o up
*Dec 27 16:37:13.027: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEth
et1/0, changed state to up
R2(config-if)#int f1/1
R2(config-if)#ip add 202.193.1.1 255.255.255.0
R2(config-if)#no shut
R2(config-if)#
*Dec 27 16:37:31.347: %LINK-3-UPDOWN: Interface FastEthernet1/1, changed stat
o up
*Dec 27 16:37:32.347: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEth
et1/1, changed state to up
R2(config-if)#exit
R2(config)#ip route 0.0.0.0 0.0.0.0 202.193.1.2
路由器R3配置如下:
R3(config)#int f1/1
R3(config-if)#ip add 202.193.1.2 255.255.255.0
R3(config-if)#no shut
R3(config-if)#
*Dec 27 16:37:49.923: %LINK-3-UPDOWN: Interface FastEthernet1/1, changed stat
o up
*Dec 27 16:37:50.923: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEth
et1/1, changed state to up
R3(config-if)#int f1/0
R3(config-if)#ip add 192.168.2.1 255.255.255.0
R3(config-if)#no shut
R3(config-if)#
*Dec 27 16:38:14.075: %LINK-3-UPDOWN: Interface FastEthernet1/0, changed stat
o up
*Dec 27 16:38:15.075: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEth
et1/0, changed state to up
R3(config-if)#exit
R3(config)#ip route 0.0.0.0 0.0.0.0 202.193.1.1
路由器R4配置如下:
R4(config)#int f1/0
R4(config-if)#ip add 192.168.2.2 255.255.255.0
R4(config-if)#no shut
R4(config-if)#
*Dec 27 16:38:31.963: %LINK-3-UPDOWN: Interface FastEthernet1/0, changed state t
o up
*Dec 27 16:38:32.963: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthern
et1/0, changed state to up
R4(config-if)#exit
R4(config)#ip route 0.0.0.0 0.0.0.0 192.168.2.1
(2) 连通性测试
路由器R1连通性测试如下:
R1(config)#do ping 192.168.2.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.2.2, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 80/115/176 ms
路由器R4连通性测试如下:
R4(config)#do ping 192.168.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.1.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 24/77/140 ms
Step 2: 配置路由器的VPN
(1) 配置路由器R2和R3上的VPN
路由器R2配置如下:
R2(config)#crypto isakmp enable //启动IKE
R2(config)#crypto isakmp policy 1 //建立IKE协商策略1
R2(config-isakmp)#authentication pre-share //使用预定义秘钥
R2(config-isakmp)#encryption des //加密算法DES
R2(config-isakmp)#hash md5 //认证算法MD5
R2(config-isakmp)#lifetime 3600 //SA的活动时间3600秒
R2(config-isakmp)#crypto isakmp key keywang address 202.193.1.2
//设置共享秘钥keywang和对端IP地址
R2(config)#crypto ipsec transform-set setwang ah-md5-hmac esp-des
//设置名为setwang的传输模式集为AH验证、ESP加密
R2(cfg-crypto-trans)#exit
R2(config)#access-list 101 permit ip any any
//配置保护访问控制列表101允许IP协议通过所有
R2(config)#crypto map mapwang 1 ipsec-isakmp
//创建名为mapwang序列优先级1的Crypto maps
% NOTE: This new crypto map will remain disabled until a peer
and a valid access list have been configured.
//提示:这个新的Crypto map将保持未启动,直到一个对端或存在的访问列表被设置好
R2(config-crypto-map)#match address 101 //配对ACL号101
R2(config-crypto-map)#set peer 202.193.1.2 //设置对端IP地址
R2(config-crypto-map)#set transform-set setwang //设置传输模式名称setwang
R2(config-crypto-map)#exit
R2(config)#int f1/1
R2(config-if)#crypto map mapwang //应用Crypto Mapsmapwang到接口
R2(config-if)#
*Dec 27 16:49:03.135: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
//网络安全联盟密钥管理协议启动
R2(config-if)#exit
路由器R3配置如下:
R3(config)#crypto isakmp enable
R3(config)#crypto isakmp policy 1
R3(config-isakmp)#authentication pre-share
R3(config-isakmp)#encryption des
R3(config-isakmp)#hash md5
R3(config-isakmp)#lifetime 3600
R3(config-isakmp)#crypto isakmp key keywang address 202.193.1.1
R3(config)#crypto ipsec transform-set setwang ah-md5-hmac esp-des
R3(cfg-crypto-trans)#exit
R3(config)#access-list 101 permit ip any any
R3(config)#crypto map mapwang 1 ipsec-isakmp
% NOTE: This new crypto map will remain disabled until a peer
and a valid access list have been configured.
R3(config-crypto-map)#match address 101
R3(config-crypto-map)#set peer 202.193.1.1
R3(config-crypto-map)#set transform-set setwang
R3(config-crypto-map)#exit
R3(config)#int f1/1
R3(config-if)#crypto map mapwang
R3(config-if)#
*Dec 27 16:54:27.799: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
R3(config-if)#exit
(2) 检查VPN设置
路由器R2设置如下:
R2(config)#do show crypto isakmp policy //查看IKE策略
Global IKE policy
Protection suite of priority 1 //优先级1的保护套件
encryption algorithm: DES - Data Encryption Standard (56 bit keys).
//加密算法:DES – 标准数据加密(56 bit密钥)
hash algorithm: Message Digest 5
//验证算法:MD5
authentication method: Pre-Shared Key
//认证方法:预定义密钥
Diffie-Hellman group: #1 (768 bit)
lifetime: 3600 seconds, no volume limit
//活动时间:3600秒,没有容量限制
Default protection suite
encryption algorithm: DES - Data Encryption Standard (56 bit keys).
hash algorithm: Secure Hash Standard
authentication method: Rivest-Shamir-Adleman Signature
Diffie-Hellman group: #1 (768 bit)
lifetime: 86400 seconds, no volume limit
R2(config)#do show crypto ipsec transform-set //查看IPSec策略
Transform set setwang: { ah-md5-hmac } //传输集设置setwang {AH验证}
will negotiate = { Tunnel, }, //将协商={通道, }
{ esp-des } //{ESP加密}
will negotiate = { Tunnel, },
R2(config)#do show crypto ipsec sa //查看SA信息
interface: FastEthernet1/1 //接口F1/1
Crypto map tag: mapwang, local addr. 202.193.1.1
//Crypto Map标签:mapwang,本地地址:202.193.1.1
protected vrf: //保护的vrf成员
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0) //本地鉴定
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)//偏远鉴定
current_peer: 202.193.1.2:500 //当前对端:202.193.1.2:500
PERMIT, flags={origin_is_acl,ipsec_sa_request_sent}
//允许,标记={ACL初始,SA请求的发送}
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest 0 //包封装/包加密/包分类
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 1, #recv errors 0
local crypto endpt.: 202.193.1.1, remote crypto endpt.: 202.193.1.2
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet1/1
current outbound spi: 0
inbound esp sas:
inbound ah sas:
inbound pcp sas:
outbound esp sas:
outbound ah sas:
outbound pcp sas:
protected vrf:
local ident (addr/mask/prot/port): (202.193.1.1/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
current_peer: 202.193.1.2:500
PERMIT, flags={}
#pkts encaps: 4, #pkts encrypt: 4, #pkts digest 4
#pkts decaps: 4, #pkts decrypt: 4, #pkts verify 4
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 202.193.1.1, remote crypto endpt.: 202.193.1.2
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet1/1
current outbound spi: B65DE175
inbound esp sas:
spi: 0x8966F923(2305227043)
transform: esp-des ,
in use settings ={Tunnel, }
slot: 0, conn id: 2002, flow_id: 1, crypto map: mapwang
sa timing: remaining key lifetime (k/sec): (4413499/3588)
IV size: 8 bytes
replay detection support: Y
inbound ah sas:
spi: 0xAACACE76(2865417846)
transform: ah-md5-hmac ,
in use settings ={Tunnel, }
slot: 0, conn id: 2000, flow_id: 1, crypto map: mapwang
sa timing: remaining key lifetime (k/sec): (4413499/3588)
replay detection support: Y
inbound pcp sas:
outbound esp sas:
spi: 0xB65DE175(3059605877)
transform: esp-des ,
in use settings ={Tunnel, }
slot: 0, conn id: 2003, flow_id: 2, crypto map: mapwang
sa timing: remaining key lifetime (k/sec): (4413499/3588)
IV size: 8 bytes
replay detection support: Y
outbound ah sas:
spi: 0x61C0644B(1639998539)
transform: ah-md5-hmac ,
in use settings ={Tunnel, }
slot: 0, conn id: 2001, flow_id: 2, crypto map: mapwang
sa timing: remaining key lifetime (k/sec): (4413499/3586)
replay detection support: Y
outbound pcp sas:
R2(config)#do show crypto map //查看加密映射
Crypto Map "mapwang" 1 ipsec-isakmp
Peer = 202.193.1.2
Extended IP access list 101
access-list 101 permit ip any any
Current peer: 202.193.1.2
Security association lifetime: 4608000 kilobytes/3600 seconds
PFS (Y/N): N
Transform sets={
setwang,
}
Interfaces using crypto map mapwang:
FastEthernet1/1
