1. Bandwidth and Delay
a. On a generic multi-hop network, explain the potential causes of delay for a packet:
? Propagation delay:
? Transmission delay:
? Queueing delay:
? Processing delay:
b. For a fixed network path, which of these delays are constant over time, and which ones vary with load? Explain why.
c. (Estimating bottleneck bandwidth). An interesting technique used to estimate the bottleneck bandwidth in a network is called packet pair. The idea is simple: you send two packets back-to-back (no gap), at the full bandwidth of the first hop. The receiver at the other end can then determine the bandwidth by measuring the delay between the receptions of the two packets. In this problem we will do just that, with a simplified 3-link network shown in the figure below, with no extra traffic, no queues, and instantaneous access to the medium.
Setup: In the figure, assume there is no queueing or processing delay, and that nodes can forward a packet as soon as (a) all bytes for the packet have been received from the previous link, and (b) the outgoing link is free. All three links have a propagation delay of 10ms; link AB has a bandwidth of 10Mbps ((107 bits per second), and link CD has a bandwidth of 8 Mbps (8 × 106 bps). You send two probe packets of 1000 bytes each, as depicted in the figure.
(a) In this setup, calculate the length of the interval t1t2 in the figure. Do the same for t3t4
(b) In the diagram, draw the transmission of the two packets in the link BC
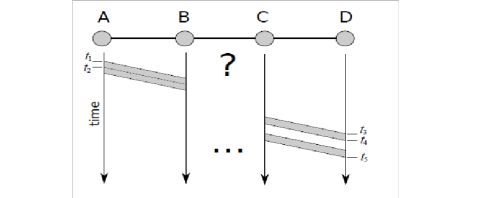
, paying attention to when they must start and when they must end.
(c) You measure the delay t4t5 between the end of the receptions of the two packets to be 8 ms. Assuming that the link BC is the bottleneck bandwidth in the path, what is its bandwidth? Explain your reasoning.
2. Answer the following questions regarding TCP, UDP, IP, and routing:
a) What are the important fields in the TCP, UDP, and IP headers? Without these fields, the protocols would clearly not “work”.
b) Sketch the TCP connection initiation and connection termination packet flows using a timing diagram.
3. Socket Programming
3.1. Consider the following Java application:
socket = new DatagramSocket(12345);
while (true) {socket.receive(packet);}
What happens if somebody decides to run two instances of this
application on one machine and 4 UDP segments arrive at port 12345?
a) both instances of the application receive all 4 segments
b) one instance receives all 4 segments
c) some segments are received by one instance, other segments are received by the other instance
d) one instance receives segments 1 and 3, the other receives segments 2 and 4
3.2. Given the following lines from a Java program segment:
byte[] dataOut = new byte [512];
String userInput = inFromUser.readLine();
dataOut = userInput.getBytes();
Which of the following lines of code could be used to create a new UDP datagram packet to send the data that was provided by the user to a host identified by the InetAddress object IPAddress?
a) DatagramPacket packetToSend = new
DatagramPacket(dataOut, dataOut.length, IPAddress)
b) UDPPacket = new UDPDatagram (userInput,
userInput.length, IPaddress, 9876)
c) DatagramPacket packet = new DatagramPacket(dataOut, dataOut.length, IPAddress, 9876)
d) Socket datagramSocket = new dataGramPacket(dataOut, IPAddress)
3.3.
Consider a server socket object
socket = ServerSocket(12345);
What does the invocation of socket.accept() return?
a) 'true' if there is a new TCP segment in the socket's buffer, false otherwise
b) a new TCP segment from the socket's buffer (blocks if no segments are available)
c) 'true' if a new TCP connection request has arrived, false otherwise d) a socket associated with a new TCP connection (blocks if no
connections are available)
3.4.
Assume the following two lines of code are to be executed on the machine blue.cse.yorku.ca:
Socket myFirstSocket = new Socket("blue.cse.yorku.ca", 5555);
Socket mySecondSocket = new Socket(5555);
Are the two lines/commands in conflict? Explain briefly!
3.5.
Suppose application A is using a UDP socket, i.e. DatagramSocket(), to transfer data to application B
on a remote host. Suppose application A calls send() method on the given socket 10 times.
a) Can the underlying network stack transmit more than 10 data packets? b) Can the underlying network stack transmit fewer than 10 data packets? Explain briefly!
4. The Transmission Control Protocol uses a method called congestion control to regulate the traffic entering the network. The behavior of TCP congestion control can be represented as a graph in which the x-axis indicates the time, and the y-axis indicates congestion window size. Please use the graph shown below to the answer the following
questions. Note that the graph does not explicitly show timeouts, but you should be able to figure out when timeouts happened based on the events shown.
(a) Slow Start: give two reasons why slow start is used, and explain why it does a better job than congestion avoidance for that function.
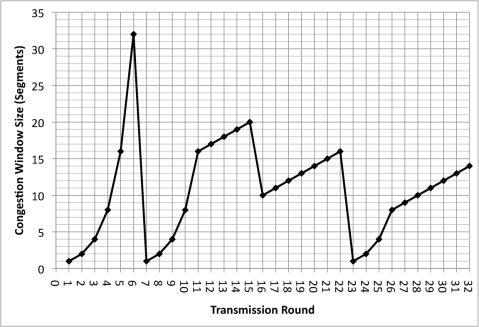
(b) Slow Start: identify the intervals of time when TCP slow start is operating. For each interval, identify which of the above reasons apply and do not apply and explain why.
(c) Congestion Avoidance: identify the intervals of time when TCP
congestion avoidance is operating. Why should congestion avoidance be used instead of slow start during these intervals? Please clearly identify one specific reason.
(d) Fast Retransmission: identify the intervals of time when TCP fast
retransmission is used. Please explain what fast retransmission does and how it is triggered.
(e) Fast Recovery: identify the intervals of time when TCP fast recovery is operating. What does fast recovery do and explain why is it beneficial.
(f) Lack of fast recovery: identify the interval(s) of time when fast recovery could have happened, but did not. Identify one specific example of a circumstance that may prevent fast recovery from happening.
5. NAT and IPv6
5.1 Assume an IP packet carrying an HTTP request is going from a local (i.e. home) area network onto the wider Internet through a NAT router. Name all header fields that the NAT router needs to change in the given packet? Explain your answer. (Hint: encapsulation as well as the syntax/semantics of all involved protocols must be taken into consideration.)
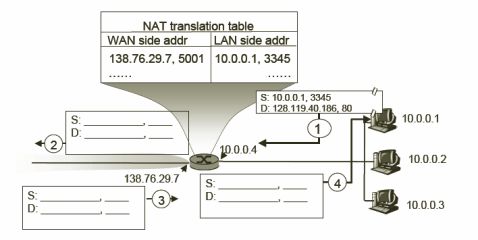
5.2 The diagram below shows a packet traveling through a NAT router. Packet 1 is sent from the internal host (S) to the NAT router, packet 2 is sent from the NAT router to the external web server (D), packet 3 is received from the web server by the NAT router, and packet 4 is sent by the NAT router to the original host. Fill in the missing source and destination IP addresses and port numbers in packets 2-4.
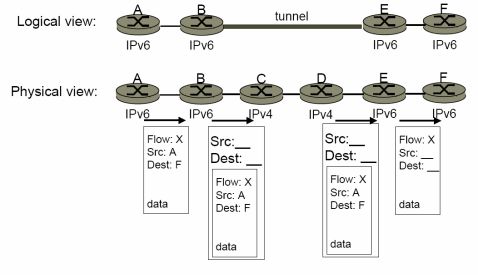
5.3 The diagram below shows an IPv6 packet tunnelled over IPv4. Fill in the
missing source and destination addresses at places/packets marked 1, 2, and 3.
6.
Consider a datagram network using 32-bit host addresses. Suppose a
router has four links, numbered 0 through 3, and packets are to be forwarded to the link interfaces as follows:
Destination Address Range Link Interface 11100000 00000000 00000000 00000000 Through (0)
11100000 00111111 11111111 11111111
11100000 01000000 00000000 00000000
Through (1)
111100000 01000000 11111111 11111111
11100000 01000001 00000000 00000000
Through (2) 11100001 01111111 11111111 11111111
Otherwise
a) Provide a forwarding table that has five entries, uses longest prefix (3) matching, and forwards packets to the correct link interfaces.
b) Describe how your forwarding table determines the appropriate link interface for datagrams with destination addresses(following): 11001000 10010001 01010001 01010101
11100001 01000000 11000011 00111100
11100001 10000000 00010001 01110111
