端口介绍:
3389端口是Windows 2000(2003) Server 的服务端口,可以通过这个端口,用"远程桌面"等连接工具来连接到远程的服务器,如果连接上了,输入系统管理员的用户名和密码后,将变得可以像操作本机一样操作远程的电脑,因此远程服务器一般都将这个端口修改数值或者关闭。
3389端口的关闭:
首先说明3389端口是windows的远程管理终端所开的端口,它并不是一个木马程序,请先确定该服务是否是你自己开放的。如果不是必须的,建议关闭该服务。
win2000 server 开始-->程序-->管理工具-->服务里找到Terminal Services服务项,选中属性选项将启动类型改成手动,并停止该服务。 win2000 pro 开始-->设置-->控制面板-->管理工具-->服务里找到Terminal Services服务项,选中属性选项将启动类型改成手动,并停止该服务。
windows xp关闭的方法:在我的电脑上点右键选属性-->远程,将里面的远程协助和远程桌面两个选项框里的勾去掉。
通过注册表关闭3389端口
开始---运行
输入regedit打开注册表
[HKEY_LOCAL_MACHINE\System\currentcontrolset\control\Terminalserver\wds\rdpwd\tds\tcp分支,选中名为portnumber的键值,将其3389改为其他(如1234)看我操作这里control有2个分别为controlSET001 和controlSET002我一个一个来 先进controlSET001在来controlSET002 下面我们在看currentcontrolset
[HKEY_LOCAL_MACHINE\System\currentcontrolset\control\Terminalserver\winstations\RDP-Tcp\PortNumber分支里应该有一个或者很多类似的子键,一样的改他的值3389为其他(如1234)
将远程桌面端口修改成其他端口号
修改服务器端的端口设置 ,注册表有2个地方需要修改。
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\Wds\rdpwd\Tds\tcp] PortNumber值,默认是3389,修改成所希望的端口,就如你所说该成6222。第二个地方:
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal
Server\WinStations\RDP-Tcp] PortNumber值,默认是3389,修改成所希望的端口,该成6222,重起一下就OK了。这样就可以了
要注意的是:当你的计算机修改完端口号后要想继续使用远程桌面,并且计算机有启用防火墙,则必须在防火墙例外中添加所修改的端口号。否则用3389与修改后的端口号都将连不上远程桌面。
3389端口是Windows 2000(2003) Server 远程桌面的服务端口,可以通过这个端口,用"远程桌面"等连接工具来连接到远程的服务器,如果连接上了,输入系统管理员的用户名和密码后,将变得可以像操作本机一样操作远程的电脑,因此远程服务器一般都将这个端口修改数值者者关闭.
修改数值的话需要修改注册表的两个地方:
第一个地方:
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\TerminalServer\Wds\rdpwd\Tds\tcp]
PortNumber值,默认是3389,修改成所希望的端口,比如6000
第二个地方:
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp]
PortNumber值,默认是3389,修改成所希望的端口,比如6000
现在这样就可以了。重启系统就可以了.
你如果觉得修改数值不够安全,可以把这个端口屏蔽掉:
一是在网卡的端口过滤里边,只开放你需要的端口,具体是在tcp/ip的属性设置里头有个"高级"按键,然后点里面最后一个"选项"按钮,在tpc/ip筛选里面,只允许你想开放的端口;
二是可以安装一个防火墙,也可以达到阻止别人访问你3389端口的目的.
怎么样开3389端口,这里我把他们总结一下,很全面,希望对你有用:
1,打开记事本,编辑内容如下:
echo [Components] > c:\sql
echo TSEnable = on >> c:\sql
sysocmgr /i:c:\winnt\inf\sysoc.inf /u:c:\sql /q
编辑好后存为BAT文件,上传至肉鸡,执行。这里值得注意的是要确定winnt是否在c盘,如果在其他盘则需要改动。
2 (对xp\2000都有效) 脚本文件 本地开3389 工具:rots1.05
使用方法:
在命令行方式下使用windows自带的脚本宿主程序cscript.exe调用脚本,例如:
c:\>cscript ROTS.vbs <目标IP> <用户名> <密码> [服务端口] [自动重起选项]
服务端口: 设置终端服务的服务端口。默认是3389。
自动重起选项: 使用/r表示安装完成后自动重起目标使设置生效。
使用/fr表示强制重起目标。(如果/r不行,可以试试这个)
使用此参数时,端口设置不能忽略。
比如扫描到了一个有NT弱口令的服务器,IP地址是222.222.222.222,管理员帐户是administrator,密码为空
运行CMD(2000下的DOS),我们给它开终端!
命令如下!
cscript reg.vbe 222.222.222.222 administrator "" 3389 /fr
上面的命令应该可以理解吧?cscript reg.vbe这是命令,后面的是IP,然后是管理员帐户,接这是密码,因为222.222.222.222 这台服务器的管理员密码是空的,那就用双引号表示为空,再后面是端口,你可以任意设置终端的端口,/fr是重启命令(强制重启,一般我都用这个,你也可以/r,这是普通重启)
脚本会判断目标系统类型,如果不是server及以上版本,就会提示你是否要取消。
因为pro版不能安装终端服务。
如果你确信脚本判断错误,就继续安装好了。
如果要对本地使用,IP地址为127.0.0.1或者一个点(用.表示),用户名和密码都为空(用""表示)。
脚本访问的目标的135端口,如果目标135端口未开放,或者WMI服务关闭,那么脚本就没用了。
3,下载3389自动安装程序-djshao正式版5.0
说明:
解压djshao5.0.zip,用你的随便什么方法把把解压出来的djxyxs.exe上传到肉鸡的c:\winnt\temp下,然后进入c:\winnt\temp目录执行djxyxs.exe解压缩文件,然后再执行解压缩出来的azzd.exe文件,等一会肉鸡会自动重启!重启后会出现终端服务!
特点:1、不用修改注册表的安装路径,注册表会自动修改,安装完后会自动恢复到原来的安装路径,2、在后台安静模式运行,就算肉鸡旁有人也没有关系!3、在添加和删除中看不出终端服务被安装的痕迹,也就是启动终端前不会打钩,4、不会在肉鸡上留下你的上传文件,在安装完终端服务后会会自动删除你上传到c:\winnt\temp下的任何文件!5、不管肉鸡的winnt装在什么盘上都无所谓!6、安装完终端后会删除在管理工具中的终端快捷图标!7、在没有安装终端前,终端服务是被禁止的!安装终端后,终端服务被改为自动!但是如果在安装前终端服务是手动!安装后就可能还是手动!等重启后就不会打开服务!所以在软件中加了sc指令,等安装完后,不管终端服务是禁止还是手动还是自动,全部改为自动。8、自动检测肉
鸡是不是服务器版,如果不是删除原文件,不执行安装,如果是服务器版就执行安装!9、支持中日韩繁四个版本的win2000服务器版!
5,下载DameWare NT Utilities 3.66.0.0 注册版
安装注册完毕后输入对方IP用户名密码,等待出现是否安装的对话框点是。
复制启动后出现对方桌面。
在对方桌面进入控制面版,点添加或删除程序。进入后点添加/删除windows组件,找到终端服务,点际进入后在启动终端服务上打上勾。确定自动提示重起,重起后OK
如何修改远程登录3389端口
2009-06-27 17:52:29| 分类: computer | 标签: |字号大中小 订阅
为了使独享服务器远程登陆更加安全,经常能够遇到客户询问如何修改远程桌面端口的问
题,下面就详细说明一下具体方法:
首先,登陆服务器选择系统桌面中的“开始”、“运行”命令,从弹出的系统运行框中,输入字符串
命令“regedit”,单击“确定”按钮后,打开本地工作站的系统注册表编辑界面;展开
HKEY_LOCAL_MACHINE注册表分支,从其后弹出的分支列表中依次选中
SYSTEM\CurrentControlSet\Control\Terminal Server\Wds\rdpwd\Tds\tcp子键
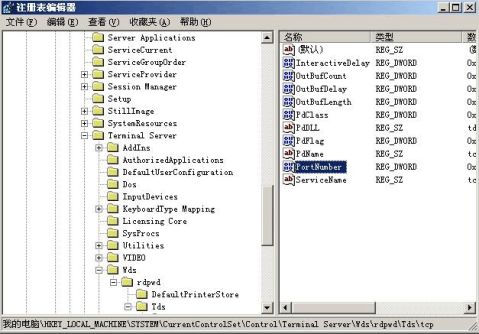
在tcp子键所对应的右侧显示区域中,我们会看到一个名为PortNumber的子键,这个子键其实就是用来定义远程桌面端口号码的,将该子键的数值设置成其他端口号码,例如可以将其数值设
置成“9999”
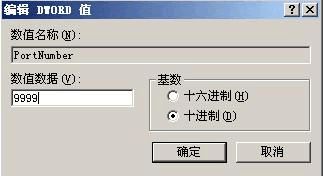
完成数值修改操作后,我们再将鼠标定位于注册表分支
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp,在RDP-Tcp子键所对应的右侧显示区域中,我们同样会看到一个名为PortNumber的子键,把该子键的数
值也要一并修改过来,例如这里我们也要将它的数值修改成“9999”
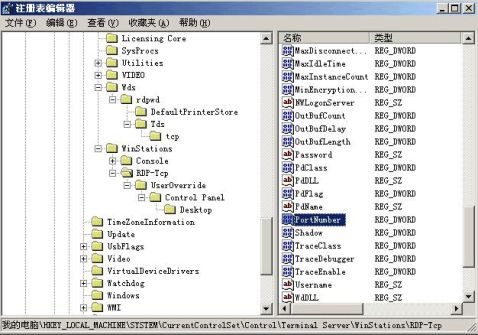
完成这两步操作后,我们就可以使用远程桌面通过ip地址加端口号的方式连接。
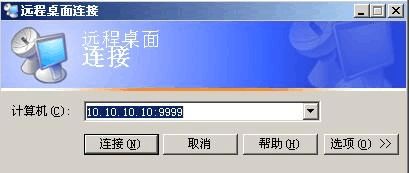
注:如果您更改了远程登陆的端口请记得在系统或者您自己安装的防火墙上打开这个例外端口。
第二篇:端口号
知名端口号
//注: 由于一些应用软件占用了部分端口, 因此此文件中的部分端口被注释掉了(注释字符为: //)
TCP 1=TCP Port Service Multiplexer TCP 2=Death
TCP 5=Remote Job Entry,yoyo TCP 7=Echo TCP 11=Skun TCP 12=Bomber TCP 16=Skun TCP 17=Skun
TCP 18=消息传输协议,skun TCP 19=Skun
TCP 20=FTP Data,Amanda TCP 21=文件传输,Back
Construction,Blade Runner,Doly Trojan,Fore,FTP trojan,Invisible FTP,Larva, WebEx,WinCrash TCP 22=远程登录协议
TCP 23=远程登录(Telnet),Tiny Telnet Server (= TTS) TCP 25=电子邮件
(SMTP),Ajan,Antigen,Email Password Sender,Happy 99,Kuang2,ProMail
trojan,Shtrilitz,Stealth,Tapiras,Terminator,WinPC,WinSpy,Haebu Coceda TCP 27=Assasin TCP 28=Amanda TCP 29=MSG ICP
TCP 30=Agent 40421
TCP 31=Agent 31,Hackers
Paradise,Masters Paradise,Agent 40421 TCP 37=Time,ADM worm TCP 39=SubSARI
TCP 41=DeepThroat,Foreplay TCP 42=Host Name Server TCP 43=WHOIS TCP 44=Arctic TCP 48=DRAT
TCP 49=主机登录协议 TCP 50=DRAT
TCP 51=IMP Logical Address Maintenance,Fuck Lamers Backdoor TCP 52=MuSka52,Skun
TCP 53=DNS,Bonk (DOS Exploit) TCP 54=MuSka52 TCP 58=DMSetup TCP 59=DMSetup TCP 63=whois++
TCP 64=Communications Integrator TCP 65=TACACS-Database Service TCP 66=Oracle SQL*NET,AL-Bareki TCP 67=Bootstrap Protocol Server TCP 68=Bootstrap Protocol Client TCP 69=W32.Evala.Worm,BackGate Kit,Nimda,Pasana,Storm,Storm worm,Theef,Worm.Cycle.a
TCP 70=Gopher服务,ADM worm TCP 79=用户查询
(Finger),Firehotcker,ADM worm TCP 80=超文本服务器(Http),Executor,RingZero
TCP 81=Chubo,Worm.Bbeagle.q TCP 82=Netsky-Z
TCP 88=Kerberos krb5服务 TCP 99=Hidden Port TCP 102=消息传输代理
TCP 108=SNA网关访问服务器 TCP 109=Pop2
TCP 110=电子邮件(Pop3),ProMail TCP 113=Kazimas, Auther Idnet TCP 115=简单文件传输协议
TCP 118=SQL Services, Infector 1.4.2 TCP 119=新闻组传输协议(Newsgroup(Nntp)), Happy 99
TCP 121=JammerKiller, Bo jammerkillah TCP 123=网络时间协议(NTP),Net Controller
TCP 129=Password Generator Protocol TCP 133=Infector 1.x
TCP 135=微软DCE RPC end-point mapper服务
TCP 137=微软Netbios Name服务(网上邻居传输文件使用)
TCP 138=微软Netbios Name服务(网上邻居传输文件使用)
TCP 139=微软Netbios Name服务(用于文件及打印机共享)
TCP 142=NetTaxi TCP 143=IMAP
TCP 146=FC Infector,Infector TCP 150=NetBIOS Session Service TCP 156=SQL服务器 TCP 161=Snmp
TCP 162=Snmp-Trap TCP 170=A-Trojan
TCP 177=X Display管理控制协议 TCP 179=Border网关协议(BGP) TCP 190=网关访问控制协议(GACP) TCP 194=Irc
TCP 197=目录定位服务(DLS) TCP 256=Nirvana
TCP 315=The Invasor
TCP 371=ClearCase版本管理软件
TCP 389=Lightweight Directory Access Protocol (LDAP)
TCP 396=Novell Netware over IP TCP 420=Breach
TCP 421=TCP Wrappers TCP 443=安全服务
TCP 444=Simple Network Paging Protocol(SNPP)
TCP 445=Microsoft-DS
TCP 455=Fatal Connections
TCP 456=Hackers paradise,FuseSpark TCP 458=苹果公司QuickTime TCP 513=Grlogin
TCP 514=RPC Backdoor TCP 520=Rip
TCP 531=Rasmin,Net666 TCP 544=kerberos kshell TCP 546=DHCP Client TCP 547=DHCP Server
TCP 548=Macintosh文件服务
TCP 555=Ini-Killer,Phase Zero,Stealth Spy
TCP 569=MSN
TCP 605=SecretService TCP 606=Noknok8 TCP 660=DeepThroat TCP 661=Noknok8
TCP 666=Attack FTP,Satanz Backdoor,Back Construction,Dark Connection Inside 1.2 TCP 667=Noknok7.2 TCP 668=Noknok6 TCP 669=DP trojan TCP 692=GayOL
TCP 707=Welchia,nachi TCP 777=AIM Spy
TCP 808=RemoteControl,WinHole TCP 815=Everyone Darling TCP 901=Backdoor.Devil TCP 911=Dark Shadow TCP 993=IMAP
TCP 999=DeepThroat TCP 1000=Der Spaeher
TCP 1001=Silencer,WebEx,Der Spaeher TCP 1003=BackDoor TCP 1010=Doly TCP 1011=Doly TCP 1012=Doly TCP 1015=Doly TCP 1016=Doly TCP 1020=Vampire
TCP 1023=Worm.Sasser.e TCP 1024=NetSpy.698(YAI) TCP 1059=nimreg
//TCP 1025=NetSpy.698,Unused Windows Services Block
//TCP 1026=Unused Windows Services Block
//TCP 1027=Unused Windows Services Block
TCP 1028=应用层网关服务
//TCP 1029=Unused Windows Services Block
//TCP 1030=Unused Windows Services Block
//TCP 1033=Netspy
//TCP 1035=Multidropper //TCP 1042=Bla //TCP 1045=Rasmin
//TCP 1047=GateCrasher //TCP 1050=MiniCommand TCP 1058=nim TCP 1069=Backdoor.TheefServer.202 TCP 1070=Voice,Psyber Stream Server,Streaming Audio Trojan TCP 1079=ASPROVATalk TCP
1080=Wingate,Worm.BugBear.B,Worm.Novarg.B
//TCP 1090=Xtreme, VDOLive //TCP 1092=LoveGate //TCP 1095=Rat //TCP 1097=Rat //TCP 1098=Rat //TCP 1099=Rat
TCP 1109=Pop with Kerberos TCP 1110=nfsd-keepalive
TCP 1111=Backdoor.AIMVision TCP 1155=Network File Access //TCP 1170=Psyber Stream
Server,Streaming Audio trojan,Voice //TCP 1200=NoBackO //TCP 1201=NoBackO //TCP 1207=Softwar
//TCP 1212=Nirvana,Visul Killer //TCP 1234=Ultors
//TCP 1243=BackDoor-G, SubSeven, SubSeven Apocalypse
//TCP 1245=VooDoo Doll
//TCP 1269=Mavericks Matrix
TCP 1270=Microsoft Operations Manager //TCP 1313=Nirvana //TCP 1349=BioNet TCP 1352=Lotus Notes
TCP 1433=Microsoft SQL Server TCP 1434=Microsoft SQL Monitor //TCP 1441=Remote Storm //TCP
1492=FTP99CMP(BackOriffice.FTP) TCP 1503=NetMeeting T.120
TCP 1512=Microsoft Windows Internet Name Service
//TCP 1509=Psyber Streaming Server TCP 1570=Orbix Daemon //TCP 1600=Shivka-Burka //TCP 1703=Exloiter 1.1
TCP 1720=NetMeeting H.233 call Setup TCP 1731=NetMeeting音频调用控制 TCP 1745=ISA Server proxy autoconfig, Remote Winsock
TCP 1801=Microsoft Message Queue //TCP 1807=SpySender
TCP 1906=Backdoor/Verify.b TCP 1907=Backdoor/Verify.b //TCP 1966=Fake FTP 2000 //TCP 1976=Custom port //TCP 1981=Shockrave
TCP 1990=stun-p1 cisco STUN Priority 1 port
TCP 1990=stun-p1 cisco STUN Priority 1 port
TCP 1991=stun-p2 cisco STUN Priority 2 port
TCP 1992=stun-p3 cisco STUN Priority 3 port,ipsendmsg IPsendmsg
TCP 1993=snmp-tcp-port cisco SNMP TCP port
TCP 1994=stun-port cisco serial tunnel port
TCP 1995=perf-port cisco perf port TCP 1996=tr-rsrb-port cisco Remote SRB port
TCP 1997=gdp-port cisco Gateway Discovery Protocol
TCP 1998=x25-svc-port cisco X.25 service (XOT)
//TCP 1999=BackDoor, TransScout
//TCP 2000=Der Spaeher,INsane Network TCP 2002=W32.Beagle. AX @mm //TCP 2001=Transmisson scout //TCP 2002=Transmisson scout //TCP 2003=Transmisson scout //TCP 2004=Transmisson scout //TCP 2005=TTransmisson scout TCP 2011=cypress TCP 2015=raid-cs
//TCP 2023=Ripper,Pass Ripper,Hack City Ripper Pro TCP 2049=NFS //TCP 2115=Bugs //TCP 2121=Nirvana
//TCP 2140=Deep Throat, The Invasor //TCP 2155=Nirvana //TCP 2208=RuX
TCP 2234=DirectPlay
//TCP 2255=Illusion Mailer //TCP 2283=HVL Rat5 //TCP 2300=PC Explorer //TCP 2311=Studio54
TCP 2556=Worm.Bbeagle.q //TCP 2565=Striker //TCP 2583=WinCrash
//TCP 2600=Digital RootBeer //TCP 2716=Prayer Trojan TCP 2745=Worm.BBeagle.k
//TCP 2773=Backdoor,SubSeven //TCP 2774=SubSeven2.1&2.2 //TCP 2801=Phineas Phucker TCP 2967=SSC Agent //TCP 2989=Rat
//TCP 3024=WinCrash trojan
TCP 3074=Microsoft Xbox game port TCP 3127=Worm.Novarg
TCP 3128=RingZero,Worm.Novarg.B //TCP 3129=Masters Paradise
TCP 3132=Microsoft Business Rule Engine Update Service
//TCP 3150=Deep Throat, The Invasor TCP 3198=Worm.Novarg //TCP 3210=SchoolBus TCP 3268=Microsoft Global Catalog TCP 3269=Microsoft Global Catalog with LDAP/SSL
TCP 3332=Worm.Cycle.a TCP 3333=Prosiak
TCP 3535=Microsoft Class Server TCP 3389=超级终端 //TCP 3456=Terror
//TCP 3459=Eclipse 2000 //TCP 3700=Portal of Doom //TCP 3791=Eclypse //TCP 3801=Eclypse
TCP 3847=Microsoft Firewall Control TCP 3996=Portal of Doom,RemoteAnything
TCP 4000=腾讯QQ客户端 TCP 4060=Portal of Doom,RemoteAnything TCP 4092=WinCrash TCP 4242=VHM
TCP 4267=SubSeven2.1&2.2 TCP 4321=BoBo
TCP 4350=Net Device
TCP 4444=Prosiak,Swift remote TCP 4500=Microsoft IPsec NAT-T, W32.HLLW.Tufas
TCP 4567=File Nail
TCP 4661=Backdoor/Surila.f TCP 4590=ICQTrojan
TCP 4899=Remote Administrator服务器 TCP 4950=ICQTrojan
TCP 5000=WindowsXP服务器,Blazer
5,Bubbel,Back Door Setup,Sockets de Troie TCP 5001=Back Door Setup, Sockets de Troie
TCP 5002=cd00r,Shaft
TCP 5011=One of the Last Trojans (OOTLT)
TCP 5025=WM Remote KeyLogger TCP
5031=Firehotcker,Metropolitan,NetMetro TCP 5032=Metropolitan TCP 5190=ICQ Query TCP 5321=Firehotcker
TCP 5333=Backage Trojan Box 3 TCP 5343=WCrat
TCP 5400=Blade Runner, BackConstruction1.2
TCP 5401=Blade Runner,Back Construction
TCP 5402=Blade Runner,Back Construction
TCP 5471=WinCrash
TCP 5512=Illusion Mailer TCP 5521=Illusion Mailer
TCP 5550=Xtcp,INsane Network TCP 5554=Worm.Sasser TCP 5555=ServeMe TCP 5556=BO Facil
TCP 5557=BO Facil TCP 5569=Robo-Hack
TCP 5598=BackDoor 2.03 TCP 5631=PCAnyWhere data TCP 5632=PCAnyWhere TCP 5637=PC Crasher TCP 5638=PC Crasher
TCP 5678=Remote Replication Agent Connection
TCP 5679=Direct Cable Connect Manager TCP 7215=BackDoor-G, SubSeven TCP 7001=Freak88,Freak2k TCP 7300=NetMonitor TCP 7301=NetMonitor
TCP 7306=NetMonitor,NetSpy 1.0 TCP 7307=NetMonitor, ProcSpy TCP 7308=NetMonitor, X Spy TCP 7323=Sygate服务器端 TCP 7424=Host Control TCP 7511=聪明基因 TCP 5698=BackDoor TCP 5714=Wincrash3
TCP 5720=Microsoft Licensing TCP 5741=WinCrash3 TCP 5742=WinCrash
TCP 5760=Portmap Remote Root Linux Exploit
TCP 5880=Y3K RAT TCP 5881=Y3K RAT TCP 5882=Y3K RAT TCP 5888=Y3K RAT TCP 5889=Y3K RAT TCP 5900=WinVnc
TCP 6000=Backdoor.AB TCP 6006=Noknok8
TCP 6073=DirectPlay8
TCP 6129=Dameware Nt Utilities服务器 TCP 6272=SecretService TCP 6267=广外女生
TCP 6400=Backdoor.AB,The Thing TCP 6500=Devil 1.03 TCP 6661=Teman
TCP 6666=TCPshell.c
TCP 6667=NT Remote Control,Wise 播放器接收端口
TCP 6668=Wise Video广播端口 TCP 6669=Vampyre
TCP 6670=DeepThroat,iPhone TCP 6671=Deep Throat 3.0 TCP 6711=SubSeven TCP 6712=SubSeven1.x TCP 6713=SubSeven TCP 6723=Mstream
TCP 6767=NT Remote Control TCP 6771=DeepThroat
TCP 6776=BackDoor-G,SubSeven,2000 Cracks
TCP 6777=Worm.BBeagle TCP 6789=Doly Trojan TCP 6838=Mstream
TCP 6883=DeltaSource TCP 6912=Shit Heep
TCP 6939=Indoctrination
TCP 6969=GateCrasher, Priority, IRC 3 TCP 6970=RealAudio,GateCrasher TCP 7000=Remote
Grab,NetMonitor,SubSeven1.x
TCP 7001=Freak88, Weblogic默认端口 TCP 7201=NetMonitor TCP 7597=Qaz
TCP 7609=Snid X2 TCP 7626=冰河
TCP 7777=The Thing
TCP 7789=Back Door Setup, ICQKiller TCP 7983=Mstream
TCP 8000=腾讯OICQ服务器端,XDMA TCP 8010=Wingate,Logfile TCP 8011=WAY2.4
TCP 8080=WWW 代理(如:Tomcat的默认端口),Ring Zero,Chubo,Worm.Novarg.B TCP 8102=网络神偷
TCP 8181=W32.Erkez.D@mm TCP 8520=W32.Socay.Worm TCP 8594=I-Worm/Bozori.a TCP 8787=BackOfrice 2000 TCP 8888=Winvnc
TCP 8897=Hack Office,Armageddon TCP 8989=Recon
TCP 9000=Netministrator TCP 9080=WebSphere TCP 9325=Mstream
TCP 9400=InCommand 1.0 TCP 9401=InCommand 1.0 TCP 9402=InCommand 1.0
TCP 9535=Remote Man Server TCP 9872=Portal of Doom TCP 9873=Portal of Doom TCP 9874=Portal of Doom TCP 9875=Portal of Doom TCP 9876=Cyber Attacker TCP 9878=TransScout TCP 9989=Ini-Killer
TCP 9898=Worm.Win32.Dabber.a TCP 9999=Prayer Trojan TCP 10067=Portal of Doom TCP 10080=Worm.Novarg.B TCP 10084=Syphillis TCP 10085=Syphillis TCP 10086=Syphillis TCP 10101=BrainSpy
TCP 10167=Portal Of Doom TCP
10168=Worm.Supnot.78858.c,Worm.LovGate.T TCP 10520=Acid Shivers TCP 10607=Coma trojan TCP 10666=Ambush TCP 11000=Senna Spy TCP 11050=Host Control
TCP 11051=Host Control
TCP 11223=Progenic,Hack '99KeyLogger TCP 11320=IMIP Channels Port TCP 11831=TROJ_LATINUS.SVR TCP 12076=Gjamer, MSH.104b TCP 12223=Hack'99 KeyLogger
TCP 12345=GabanBus, NetBus 1.6/1.7, Pie Bill Gates, X-bill
TCP 12346=GabanBus, NetBus 1.6/1.7, X-bill
TCP 12349=BioNet
TCP 12361=Whack-a-mole TCP 12362=Whack-a-mole TCP 12363=Whack-a-mole TCP 12378=W32/Gibe@MM TCP 12456=NetBus
TCP 12623=DUN Control TCP 12624=Buttman
TCP 12631=WhackJob, WhackJob.NB1.7 TCP 12701=Eclipse2000 TCP 12754=Mstream TCP 13000=Senna Spy
TCP 13010=Hacker Brazil TCP 13013=Psychward
TCP 13223=Tribal Voice的聊天程序PowWow
TCP 13700=Kuang2 The Virus TCP 14456=Solero
TCP 14500=PC Invader TCP 14501=PC Invader TCP 14502=PC Invader TCP 14503=PC Invader TCP 15000=NetDaemon 1.0 TCP 15092=Host Control TCP 15104=Mstream TCP 16484=Mosucker
TCP 16660=Stacheldraht (DDoS) TCP 16772=ICQ Revenge TCP 16959=Priority TCP 16969=Priority
TCP 17027=提供广告服务的Conducent"adbot"共享软件 TCP 17166=Mosaic
TCP 17300=Kuang2 The Virus TCP 17490=CrazyNet TCP 17500=CrazyNet
TCP 17569=Infector 1.4.x + 1.6.x TCP 17777=Nephron
TCP 18753=Shaft (DDoS) TCP 19191=蓝色火焰 TCP 19864=ICQ Revenge
TCP 20000=Millennium II (GrilFriend) TCP 20001=Millennium II (GrilFriend) TCP 20002=AcidkoR
TCP 20034=NetBus 2 Pro TCP 20168=Lovgate
TCP 20203=Logged,Chupacabra TCP 20331=Bla
TCP 20432=Shaft (DDoS) TCP 20808=Worm.LovGate.v.QQ
TCP 21335=Tribal Flood Network,Trinoo TCP 21544=Schwindler 1.82,GirlFriend TCP 21554=Schwindler
1.82,GirlFriend,Exloiter 1.0.1.2
TCP 22222=Prosiak,RuX Uploader 2.0 TCP 22784=Backdoor.Intruzzo TCP 23432=Asylum 0.1.3 TCP 23444=网络公牛
TCP 23456=Evil FTP, Ugly FTP, WhackJob TCP 23476=Donald Dick TCP 23477=Donald Dick TCP 23777=INet Spy TCP 26274=Delta
TCP 26681=Spy Voice
TCP 27374=Sub Seven 2.0+, Backdoor.Baste
TCP 27444=Tribal Flood Network,Trinoo TCP 27665=Tribal Flood Network,Trinoo TCP 29431=Hack Attack TCP 29432=Hack Attack TCP 29104=Host Control
TCP 29559=TROJ_LATINUS.SVR TCP 29891=The Unexplained TCP 30001=Terr0r32
TCP 30003=Death,Lamers Death TCP 30029=AOL trojan
TCP 30100=NetSphere 1.27a,NetSphere 1.31
TCP 30101=NetSphere 1.31,NetSphere 1.27a
TCP 30102=NetSphere 1.27a,NetSphere 1.31
TCP 30103=NetSphere 1.31 TCP 30303=Sockets de Troie TCP 30722=W32.Esbot.A TCP 30947=Intruse TCP 30999=Kuang2 TCP 31336=Bo Whack
TCP 31337=Baron Night,BO
client,BO2,Bo Facil,BackFire,Back Orifice,DeepBO,Freak2k,NetSpy
TCP 31338=NetSpy,Back Orifice,DeepBO TCP 31339=NetSpy DK TCP 31554=Schwindler TCP 31666=BOWhack
TCP 31778=Hack Attack TCP 31785=Hack Attack TCP 31787=Hack Attack TCP 31789=Hack Attack 更新时间: 20xx年8月6日 TCP 31791=Hack Attack TCP 31792=Hack Attack TCP 32100=PeanutBrittle TCP 32418=Acid Battery
TCP 33333=Prosiak,Blakharaz 1.0 TCP 33577=Son Of Psychward TCP 33777=Son Of Psychward TCP 33911=Spirit 2001a
TCP 34324=BigGluck,TN,Tiny Telnet Server
TCP 34555=Trin00 (Windows) (DDoS) TCP 35555=Trin00 (Windows) (DDoS) TCP 36794=Worm.Bugbear-A TCP 37651=YAT
TCP 40412=The Spy
TCP 40421=Agent 40421,Masters Paradise.96
TCP 40422=Masters Paradise TCP 40423=Masters Paradise.97 TCP 40425=Masters Paradise
TCP 40426=Masters Paradise 3.x TCP 41666=Remote Boot
TCP 43210=Schoolbus 1.6/2.0 TCP 44444=Delta Source TCP 44445=Happypig TCP 45576=未知代理 TCP 47252=Prosiak TCP 47262=Delta
TCP 47624=Direct Play Server TCP 47878=BirdSpy2
TCP 49301=Online Keylogger TCP 50505=Sockets de Troie TCP 50766=Fore, Schwindler TCP 51966=CafeIni
TCP 53001=Remote Windows Shutdown TCP 53217=Acid Battery 2000 TCP 54283=Back Door-G, Sub7
TCP 54320=Back Orifice 2000,Sheep TCP 54321=School Bus .69-1.11,Sheep, BO2K
TCP 57341=NetRaider
TCP 58008=BackDoor.Tron TCP 58009=BackDoor.Tron TCP 58339=ButtFunnel
TCP 59211=BackDoor.DuckToy TCP 60000=Deep Throat TCP 60068=Xzip 6000068 TCP 60411=Connection
TCP 60606=TROJ_BCKDOR.G2.A TCP 61466=Telecommando TCP 61603=Bunker-kill TCP 63485=Bunker-kill TCP 65000=Devil, DDoS
TCP 65432=Th3tr41t0r, The Traitor TCP 65530=TROJ_WINMITE.10
TCP 65535=RC,Adore Worm/Linux TCP 69123=ShitHeep
TCP 88798=Armageddon,Hack Office UDP 1=Sockets des Troie UDP 9=Chargen UDP 19=Chargen UDP 69=Pasana UDP 80=Penrox
UDP 371=ClearCase版本管理软件
UDP 445=公共Internet文件系统(CIFS) UDP 500=Internet密钥交换
UDP 1025=Maverick's Matrix 1.2 - 2.0 UDP 1026=Remote Explorer 2000 UDP 1027=HP服务,UC聊天软件,Trojan.Huigezi.e
UDP 1028=应用层网关服务,KiLo,SubSARI UDP 1029=SubSARI UDP 1031=Xot
UDP 1032=Akosch4 UDP 1104=RexxRave UDP 1111=Daodan UDP 1116=Lurker
UDP 1122=Last 2000,Singularity UDP 1183=Cyn,SweetHeart UDP 1200=NoBackO UDP 1201=NoBackO UDP 1342=BLA trojan UDP 1344=Ptakks UDP 1349=BO dll
UDP 1512=Microsoft Windows Internet Name Service
UDP 1561=MuSka52
UDP 1772=NetControle
UDP 1801=Microsoft Message Queue UDP 1978=Slapper
UDP 1985=Black Diver
UDP 2000=A-trojan,Fear,Force,GOTHIC Intruder,Last 2000,Real 2000 UDP 2001=Scalper UDP 2002=Slapper UDP 2015=raid-cs UDP 2018=rellpack
UDP 2130=Mini BackLash
UDP 2140=Deep Throat,Foreplay,The Invasor UDP
2222=SweetHeart,Way,Backdoor/Mifeng.t UDP 2234=DirectPlay UDP 2339=Voice Spy UDP 2702=Black Diver UDP 2989=RAT
UDP 3074=Microsoft Xbox game port UDP 3132=Microsoft Business Rule Engine Update Service UDP 3150=Deep Throat UDP 3215=XHX
UDP 3268=Microsoft Global Catalog UDP 3269=Microsoft Global Catalog with LDAP/SSL
UDP 3333=Daodan
UDP 3535=Microsoft Class Server UDP 3801=Eclypse
UDP 3996=Remote Anything UDP 4128=RedShad UDP 4156=Slapper UDP 4350=Net Device
UDP 4500=Microsoft IPsec NAT-T, sae-urn
UDP 5419=DarkSky
UDP 5503=Remote Shell Trojan UDP 5555=Daodan
UDP 5678=Remote Replication Agent Connection
UDP 5679=Direct Cable Connect Manager 知名端口号
//注: 由于一些应用软件占用了部分端口, 因此此文件中的部分端口被注释掉了(注释字 UDP 5720=Microsoft Licensing UDP 5882=Y3K RAT UDP 5888=Y3K RAT
UDP 6073=DirectPlay8
UDP 6112=Battle. net Game UDP 6666=KiLo UDP 6667=KiLo UDP 6766=KiLo
UDP 6767=KiLo,UandMe
UDP 6838=Mstream Agent-handler UDP 7028=未知木马
UDP 7424=Host Control UDP 7788=Singularity
UDP 7983=MStream handler-agent UDP 8012=Ptakks
UDP 8090=Aphex's Remote Packet Sniffer UDP 8127=9_119,Chonker UDP 8488=KiLo UDP 8489=KiLo
UDP 8787=BackOrifice 2000 UDP 8879=BackOrifice 2000
UDP 9325=MStream Agent-handler UDP 10000=XHX
UDP 10067=Portal of Doom UDP 10084=Syphillis UDP 10100=Slapper
UDP 10167=Portal of Doom UDP 10498=Mstream UDP 10666=Ambush UDP 11225=Cyn
UDP 12321=Protoss
UDP 12345=BlueIce 2000 UDP 12378=W32/Gibe@MM
UDP 12623=ButtMan,DUN Control UDP 11320=IMIP Channels Port
UDP 15210=UDP remote shell backdoor server
UDP 15486=KiLo UDP 16514=KiLo UDP 16515=KiLo
UDP 18753=Shaft handler to Agent UDP 20433=Shaft
UDP 21554=GirlFriend
UDP 22784=Backdoor.Intruzzo UDP 23476=Donald Dick UDP 25123=MOTD
UDP 26274=Delta Source UDP 26374=Sub-7 2.1 UDP 26444=Trin00/TFN2K UDP 26573=Sub-7 2.1
UDP 27184=Alvgus trojan 2000 UDP 27444=Trinoo UDP 29589=KiLo
UDP 29891=The Unexplained UDP 30103=NetSphere
UDP 31320=Little Witch 符为: //)
TCP 1=TCP Port Service Multiplexer TCP 2=Death
TCP 5=Remote Job Entry,yoyo TCP 7=Echo TCP 11=Skun TCP 12=Bomber TCP 16=Skun TCP 17=Skun
TCP 18=消息传输协议,skun TCP 19=Skun
TCP 20=FTP Data,Amanda TCP 21=文件传输,Back
Construction,Blade Runner,Doly Trojan,Fore,FTP trojan,Invisible FTP,Larva, WebEx,WinCrash TCP 22=远程登录协议
TCP 23=远程登录(Telnet),Tiny Telnet Server (= TTS) TCP 25=电子邮件
(SMTP),Ajan,Antigen,Email Password Sender,Happy 99,Kuang2,ProMail
trojan,Shtrilitz,Stealth,Tapiras,Terminator,WinPC,WinSpy,Haebu Coceda TCP 27=Assasin TCP 28=Amanda TCP 29=MSG ICP
TCP 30=Agent 40421
TCP 31=Agent 31,Hackers
Paradise,Masters Paradise,Agent 40421 TCP 37=Time,ADM worm TCP 39=SubSARI
TCP 41=DeepThroat,Foreplay TCP 42=Host Name Server TCP 43=WHOIS TCP 44=Arctic TCP 48=DRAT
TCP 49=主机登录协议 TCP 50=DRAT
TCP 51=IMP Logical Address Maintenance,Fuck Lamers Backdoor TCP 52=MuSka52,Skun
TCP 53=DNS,Bonk (DOS Exploit) TCP 54=MuSka52 TCP 58=DMSetup TCP 59=DMSetup TCP 63=whois++
TCP 64=Communications Integrator TCP 65=TACACS-Database Service TCP 66=Oracle SQL*NET,AL-Bareki TCP 67=Bootstrap Protocol Server TCP 68=Bootstrap Protocol Client TCP 69=W32.Evala.Worm,BackGate Kit,Nimda,Pasana,Storm,Storm worm,Theef,Worm.Cycle.a
TCP 70=Gopher服务,ADM worm
TCP 79=用户查询
(Finger),Firehotcker,ADM worm TCP 80=超文本服务器(Http),Executor,RingZero
TCP 81=Chubo,Worm.Bbeagle.q TCP 82=Netsky-Z
TCP 88=Kerberos krb5服务 TCP 99=Hidden Port TCP 102=消息传输代理
TCP 108=SNA网关访问服务器 TCP 109=Pop2
TCP 110=电子邮件(Pop3),ProMail TCP 113=Kazimas, Auther Idnet TCP 115=简单文件传输协议
TCP 118=SQL Services, Infector 1.4.2 TCP 119=新闻组传输协议(Newsgroup(Nntp)), Happy 99
TCP 121=JammerKiller, Bo jammerkillah TCP 123=网络时间协议(NTP),Net Controller
TCP 129=Password Generator Protocol TCP 133=Infector 1.x
TCP 135=微软DCE RPC end-point mapper服务
TCP 137=微软Netbios Name服务(网上邻居传输文件使用)
TCP 138=微软Netbios Name服务(网上邻居传输文件使用)
TCP 139=微软Netbios Name服务(用于文件及打印机共享)
TCP 142=NetTaxi TCP 143=IMAP
TCP 146=FC Infector,Infector TCP 150=NetBIOS Session Service TCP 156=SQL服务器 TCP 161=Snmp
TCP 162=Snmp-Trap TCP 170=A-Trojan
TCP 177=X Display管理控制协议 TCP 179=Border网关协议(BGP) TCP 190=网关访问控制协议(GACP) TCP 194=Irc
TCP 197=目录定位服务(DLS) TCP 256=Nirvana
TCP 315=The Invasor
TCP 371=ClearCase版本管理软件
TCP 389=Lightweight Directory Access Protocol (LDAP)
TCP 396=Novell Netware over IP TCP 420=Breach
TCP 421=TCP Wrappers TCP 443=安全服务
TCP 444=Simple Network Paging Protocol(SNPP)
TCP 445=Microsoft-DS
TCP 455=Fatal Connections
TCP 456=Hackers paradise,FuseSpark TCP 458=苹果公司QuickTime TCP 513=Grlogin TCP 514=RPC Backdoor TCP 520=Rip
TCP 531=Rasmin,Net666 TCP 544=kerberos kshell TCP 546=DHCP Client TCP 547=DHCP Server
TCP 548=Macintosh文件服务
TCP 555=Ini-Killer,Phase Zero,Stealth Spy
TCP 569=MSN
TCP 605=SecretService TCP 606=Noknok8 TCP 660=DeepThroat TCP 661=Noknok8
TCP 666=Attack FTP,Satanz Backdoor,Back Construction,Dark Connection Inside 1.2 TCP 667=Noknok7.2 TCP 668=Noknok6 TCP 669=DP trojan TCP 692=GayOL
TCP 707=Welchia,nachi TCP 777=AIM Spy
TCP 808=RemoteControl,WinHole TCP 815=Everyone Darling TCP 901=Backdoor.Devil TCP 911=Dark Shadow TCP 993=IMAP
TCP 999=DeepThroat TCP 1000=Der Spaeher
TCP 1001=Silencer,WebEx,Der Spaeher TCP 1003=BackDoor TCP 1010=Doly TCP 1011=Doly TCP 1012=Doly TCP 1015=Doly TCP 1016=Doly TCP 1020=Vampire
TCP 1023=Worm.Sasser.e TCP 1024=NetSpy.698(YAI) TCP 1059=nimreg
//TCP 1025=NetSpy.698,Unused Windows Services Block
//TCP 1026=Unused Windows Services Block
//TCP 1027=Unused Windows Services Block
TCP 1028=应用层网关服务
//TCP 1029=Unused Windows Services Block
//TCP 1030=Unused Windows Services Block
//TCP 1033=Netspy
//TCP 1035=Multidropper //TCP 1042=Bla //TCP 1045=Rasmin
//TCP 1047=GateCrasher //TCP 1050=MiniCommand TCP 1058=nim
TCP 1069=Backdoor.TheefServer.202 TCP 1070=Voice,Psyber Stream Server,Streaming Audio Trojan TCP 1079=ASPROVATalk TCP
1080=Wingate,Worm.BugBear.B,Worm.Novarg.B
//TCP 1090=Xtreme, VDOLive //TCP 1092=LoveGate //TCP 1095=Rat //TCP 1097=Rat //TCP 1098=Rat //TCP 1099=Rat
TCP 1109=Pop with Kerberos TCP 1110=nfsd-keepalive
TCP 1111=Backdoor.AIMVision TCP 1155=Network File Access //TCP 1170=Psyber Stream
Server,Streaming Audio trojan,Voice //TCP 1200=NoBackO //TCP 1201=NoBackO //TCP 1207=Softwar
//TCP 1212=Nirvana,Visul Killer //TCP 1234=Ultors
//TCP 1243=BackDoor-G, SubSeven, SubSeven Apocalypse
//TCP 1245=VooDoo Doll
//TCP 1269=Mavericks Matrix
TCP 1270=Microsoft Operations Manager //TCP 1313=Nirvana //TCP 1349=BioNet TCP 1352=Lotus Notes
TCP 1433=Microsoft SQL Server TCP 1434=Microsoft SQL Monitor //TCP 1441=Remote Storm //TCP
1492=FTP99CMP(BackOriffice.FTP) TCP 1503=NetMeeting T.120
TCP 1512=Microsoft Windows Internet Name Service
//TCP 1509=Psyber Streaming Server TCP 1570=Orbix Daemon //TCP 1600=Shivka-Burka //TCP 1703=Exloiter 1.1
TCP 1720=NetMeeting H.233 call Setup TCP 1731=NetMeeting音频调用控制 TCP 1745=ISA Server proxy autoconfig, Remote Winsock
TCP 1801=Microsoft Message Queue //TCP 1807=SpySender
TCP 1906=Backdoor/Verify.b TCP 1907=Backdoor/Verify.b //TCP 1966=Fake FTP 2000 //TCP 1976=Custom port //TCP 1981=Shockrave
TCP 1990=stun-p1 cisco STUN Priority 1 port
TCP 1990=stun-p1 cisco STUN Priority 1 port TCP 1991=stun-p2 cisco STUN Priority 2 port
TCP 1992=stun-p3 cisco STUN Priority 3 port,ipsendmsg IPsendmsg
TCP 1993=snmp-tcp-port cisco SNMP TCP port
TCP 1994=stun-port cisco serial tunnel port
TCP 1995=perf-port cisco perf port TCP 1996=tr-rsrb-port cisco Remote SRB port
TCP 1997=gdp-port cisco Gateway Discovery Protocol
TCP 1998=x25-svc-port cisco X.25 service (XOT)
//TCP 1999=BackDoor, TransScout
//TCP 2000=Der Spaeher,INsane Network TCP 2002=W32.Beagle. AX @mm //TCP 2001=Transmisson scout //TCP 2002=Transmisson scout //TCP 2003=Transmisson scout //TCP 2004=Transmisson scout //TCP 2005=TTransmisson scout TCP 2011=cypress TCP 2015=raid-cs
//TCP 2023=Ripper,Pass Ripper,Hack City Ripper Pro TCP 2049=NFS //TCP 2115=Bugs //TCP 2121=Nirvana
//TCP 2140=Deep Throat, The Invasor //TCP 2155=Nirvana //TCP 2208=RuX
TCP 2234=DirectPlay
//TCP 2255=Illusion Mailer //TCP 2283=HVL Rat5 //TCP 2300=PC Explorer //TCP 2311=Studio54
TCP 2556=Worm.Bbeagle.q //TCP 2565=Striker //TCP 2583=WinCrash
//TCP 2600=Digital RootBeer //TCP 2716=Prayer Trojan TCP 2745=Worm.BBeagle.k
//TCP 2773=Backdoor,SubSeven //TCP 2774=SubSeven2.1&2.2 //TCP 2801=Phineas Phucker TCP 2967=SSC Agent //TCP 2989=Rat
//TCP 3024=WinCrash trojan
TCP 3074=Microsoft Xbox game port TCP 3127=Worm.Novarg
TCP 3128=RingZero,Worm.Novarg.B //TCP 3129=Masters Paradise
TCP 3132=Microsoft Business Rule Engine Update Service
//TCP 3150=Deep Throat, The Invasor TCP 3198=Worm.Novarg //TCP 3210=SchoolBus
TCP 3268=Microsoft Global Catalog TCP 3269=Microsoft Global Catalog with LDAP/SSL
TCP 3332=Worm.Cycle.a TCP 3333=Prosiak
TCP 3535=Microsoft Class Server TCP 3389=超级终端 //TCP 3456=Terror
//TCP 3459=Eclipse 2000 //TCP 3700=Portal of Doom //TCP 3791=Eclypse //TCP 3801=Eclypse
TCP 3847=Microsoft Firewall Control TCP 3996=Portal of Doom,RemoteAnything
TCP 4000=腾讯QQ客户端 TCP 4060=Portal of Doom,RemoteAnything TCP 4092=WinCrash TCP 4242=VHM
TCP 4267=SubSeven2.1&2.2 TCP 4321=BoBo
TCP 4350=Net Device
TCP 4444=Prosiak,Swift remote TCP 4500=Microsoft IPsec NAT-T, W32.HLLW.Tufas
TCP 4567=File Nail
TCP 4661=Backdoor/Surila.f TCP 4590=ICQTrojan
TCP 4899=Remote Administrator服务器 TCP 4950=ICQTrojan
TCP 5000=WindowsXP服务器,Blazer
5,Bubbel,Back Door Setup,Sockets de Troie TCP 5001=Back Door Setup, Sockets de Troie
TCP 5002=cd00r,Shaft
TCP 5011=One of the Last Trojans (OOTLT)
TCP 5025=WM Remote KeyLogger TCP
5031=Firehotcker,Metropolitan,NetMetro TCP 5032=Metropolitan TCP 5190=ICQ Query TCP 5321=Firehotcker
TCP 5333=Backage Trojan Box 3 TCP 5343=WCrat
TCP 5400=Blade Runner, BackConstruction1.2
TCP 5401=Blade Runner,Back Construction
TCP 5402=Blade Runner,Back Construction
TCP 5471=WinCrash
TCP 5512=Illusion Mailer TCP 5521=Illusion Mailer
TCP 5550=Xtcp,INsane Network TCP 5554=Worm.Sasser TCP 5555=ServeMe TCP 5556=BO Facil TCP 5557=BO Facil TCP 5569=Robo-Hack
TCP 5598=BackDoor 2.03 TCP 5631=PCAnyWhere data TCP 5632=PCAnyWhere TCP 5637=PC Crasher TCP 5638=PC Crasher
TCP 5678=Remote Replication Agent Connection
TCP 5679=Direct Cable Connect Manager TCP 5698=BackDoor TCP 5714=Wincrash3
TCP 5720=Microsoft Licensing TCP 5741=WinCrash3 TCP 5742=WinCrash
TCP 5760=Portmap Remote Root Linux Exploit
TCP 5880=Y3K RAT TCP 5881=Y3K RAT TCP 5882=Y3K RAT TCP 5888=Y3K RAT TCP 5889=Y3K RAT TCP 5900=WinVnc
TCP 6000=Backdoor.AB TCP 6006=Noknok8
TCP 6073=DirectPlay8
TCP 6129=Dameware Nt Utilities服务器 TCP 6272=SecretService TCP 6267=广外女生
TCP 6400=Backdoor.AB,The Thing TCP 6500=Devil 1.03 TCP 6661=Teman
TCP 6666=TCPshell.c
TCP 6667=NT Remote Control,Wise 播放器接收端口
TCP 6668=Wise Video广播端口 TCP 6669=Vampyre
TCP 6670=DeepThroat,iPhone TCP 6671=Deep Throat 3.0 TCP 6711=SubSeven TCP 6712=SubSeven1.x TCP 6713=SubSeven TCP 6723=Mstream
TCP 6767=NT Remote Control TCP 6771=DeepThroat
TCP 6776=BackDoor-G,SubSeven,2000 Cracks
TCP 6777=Worm.BBeagle TCP 6789=Doly Trojan TCP 6838=Mstream
TCP 6883=DeltaSource TCP 6912=Shit Heep
TCP 6939=Indoctrination
TCP 6969=GateCrasher, Priority, IRC 3 TCP 6970=RealAudio,GateCrasher TCP 7000=Remote
Grab,NetMonitor,SubSeven1.x
TCP 7001=Freak88, Weblogic默认端口 TCP 7201=NetMonitor
TCP 7215=BackDoor-G, SubSeven TCP 7001=Freak88,Freak2k TCP 7300=NetMonitor TCP 7301=NetMonitor
TCP 7306=NetMonitor,NetSpy 1.0 TCP 7307=NetMonitor, ProcSpy TCP 7308=NetMonitor, X Spy TCP 7323=Sygate服务器端 TCP 7424=Host Control TCP 7511=聪明基因 TCP 7597=Qaz
TCP 7609=Snid X2 TCP 7626=冰河
TCP 7777=The Thing
TCP 7789=Back Door Setup, ICQKiller TCP 7983=Mstream
TCP 8000=腾讯OICQ服务器端,XDMA TCP 8010=Wingate,Logfile TCP 8011=WAY2.4
TCP 8080=WWW 代理(如:Tomcat的默认端口),Ring Zero,Chubo,Worm.Novarg.B TCP 8102=网络神偷
TCP 8181=W32.Erkez.D@mm TCP 8520=W32.Socay.Worm TCP 8594=I-Worm/Bozori.a TCP 8787=BackOfrice 2000 TCP 8888=Winvnc
TCP 8897=Hack Office,Armageddon TCP 8989=Recon
TCP 9000=Netministrator TCP 9080=WebSphere TCP 9325=Mstream
TCP 9400=InCommand 1.0 TCP 9401=InCommand 1.0 TCP 9402=InCommand 1.0
TCP 9535=Remote Man Server TCP 9872=Portal of Doom TCP 9873=Portal of Doom TCP 9874=Portal of Doom TCP 9875=Portal of Doom TCP 9876=Cyber Attacker TCP 9878=TransScout TCP 9989=Ini-Killer
TCP 9898=Worm.Win32.Dabber.a TCP 9999=Prayer Trojan TCP 10067=Portal of Doom TCP 10080=Worm.Novarg.B TCP 10084=Syphillis TCP 10085=Syphillis TCP 10086=Syphillis TCP 10101=BrainSpy
TCP 10167=Portal Of Doom TCP
10168=Worm.Supnot.78858.c,Worm.LovGate.T TCP 10520=Acid Shivers TCP 10607=Coma trojan TCP 10666=Ambush TCP 11000=Senna Spy TCP 11050=Host Control TCP 11051=Host Control
TCP 11223=Progenic,Hack '99KeyLogger TCP 11320=IMIP Channels Port TCP 11831=TROJ_LATINUS.SVR TCP 12076=Gjamer, MSH.104b TCP 12223=Hack'99 KeyLogger
TCP 12345=GabanBus, NetBus 1.6/1.7, Pie Bill Gates, X-bill
TCP 12346=GabanBus, NetBus 1.6/1.7, X-bill
TCP 12349=BioNet
TCP 12361=Whack-a-mole TCP 12362=Whack-a-mole TCP 12363=Whack-a-mole TCP 12378=W32/Gibe@MM TCP 12456=NetBus
TCP 12623=DUN Control TCP 12624=Buttman
TCP 12631=WhackJob, WhackJob.NB1.7 TCP 12701=Eclipse2000 TCP 12754=Mstream TCP 13000=Senna Spy
TCP 13010=Hacker Brazil TCP 13013=Psychward
TCP 13223=Tribal Voice的聊天程序PowWow
TCP 13700=Kuang2 The Virus TCP 14456=Solero
TCP 14500=PC Invader TCP 14501=PC Invader TCP 14502=PC Invader TCP 14503=PC Invader TCP 15000=NetDaemon 1.0 TCP 15092=Host Control TCP 15104=Mstream TCP 16484=Mosucker
TCP 16660=Stacheldraht (DDoS) TCP 16772=ICQ Revenge TCP 16959=Priority TCP 16969=Priority
TCP 17027=提供广告服务的Conducent"adbot"共享软件 TCP 17166=Mosaic
TCP 17300=Kuang2 The Virus TCP 17490=CrazyNet TCP 17500=CrazyNet
TCP 17569=Infector 1.4.x + 1.6.x TCP 17777=Nephron
TCP 18753=Shaft (DDoS) TCP 19191=蓝色火焰 TCP 19864=ICQ Revenge
TCP 20000=Millennium II (GrilFriend) TCP 20001=Millennium II (GrilFriend) TCP 20002=AcidkoR
TCP 20034=NetBus 2 Pro TCP 20168=Lovgate
TCP 20203=Logged,Chupacabra TCP 20331=Bla
TCP 20432=Shaft (DDoS)
TCP 20808=Worm.LovGate.v.QQ
TCP 21335=Tribal Flood Network,Trinoo TCP 21544=Schwindler 1.82,GirlFriend TCP 21554=Schwindler
1.82,GirlFriend,Exloiter 1.0.1.2
TCP 22222=Prosiak,RuX Uploader 2.0 TCP 22784=Backdoor.Intruzzo TCP 23432=Asylum 0.1.3 TCP 23444=网络公牛
TCP 23456=Evil FTP, Ugly FTP, WhackJob TCP 23476=Donald Dick TCP 23477=Donald Dick TCP 23777=INet Spy TCP 26274=Delta
TCP 26681=Spy Voice
TCP 27374=Sub Seven 2.0+, Backdoor.Baste
TCP 27444=Tribal Flood Network,Trinoo TCP 27665=Tribal Flood Network,Trinoo TCP 29431=Hack Attack TCP 29432=Hack Attack TCP 29104=Host Control
TCP 29559=TROJ_LATINUS.SVR TCP 29891=The Unexplained TCP 30001=Terr0r32
TCP 30003=Death,Lamers Death TCP 30029=AOL trojan
TCP 30100=NetSphere 1.27a,NetSphere 1.31
TCP 30101=NetSphere 1.31,NetSphere 1.27a
TCP 30102=NetSphere 1.27a,NetSphere 1.31
TCP 30103=NetSphere 1.31 TCP 30303=Sockets de Troie TCP 30722=W32.Esbot.A TCP 30947=Intruse TCP 30999=Kuang2 TCP 31336=Bo Whack
TCP 31337=Baron Night,BO
client,BO2,Bo Facil,BackFire,Back Orifice,DeepBO,Freak2k,NetSpy
TCP 31338=NetSpy,Back Orifice,DeepBO TCP 31339=NetSpy DK TCP 31554=Schwindler TCP 31666=BOWhack
TCP 31778=Hack Attack TCP 31785=Hack Attack TCP 31787=Hack Attack TCP 31789=Hack Attack 更新时间: 20xx年8月6日 TCP 31791=Hack Attack TCP 31792=Hack Attack TCP 32100=PeanutBrittle TCP 32418=Acid Battery
TCP 33333=Prosiak,Blakharaz 1.0 TCP 33577=Son Of Psychward TCP 33777=Son Of Psychward TCP 33911=Spirit 2001a TCP 34324=BigGluck,TN,Tiny Telnet Server
TCP 34555=Trin00 (Windows) (DDoS) TCP 35555=Trin00 (Windows) (DDoS) TCP 36794=Worm.Bugbear-A TCP 37651=YAT
TCP 40412=The Spy
TCP 40421=Agent 40421,Masters Paradise.96
TCP 40422=Masters Paradise TCP 40423=Masters Paradise.97 TCP 40425=Masters Paradise
TCP 40426=Masters Paradise 3.x TCP 41666=Remote Boot
TCP 43210=Schoolbus 1.6/2.0 TCP 44444=Delta Source TCP 44445=Happypig TCP 45576=未知代理 TCP 47252=Prosiak TCP 47262=Delta
TCP 47624=Direct Play Server TCP 47878=BirdSpy2
TCP 49301=Online Keylogger TCP 50505=Sockets de Troie TCP 50766=Fore, Schwindler TCP 51966=CafeIni
TCP 53001=Remote Windows Shutdown TCP 53217=Acid Battery 2000 TCP 54283=Back Door-G, Sub7
TCP 54320=Back Orifice 2000,Sheep TCP 54321=School Bus .69-1.11,Sheep, BO2K
TCP 57341=NetRaider
TCP 58008=BackDoor.Tron TCP 58009=BackDoor.Tron TCP 58339=ButtFunnel
TCP 59211=BackDoor.DuckToy TCP 60000=Deep Throat TCP 60068=Xzip 6000068 TCP 60411=Connection
TCP 60606=TROJ_BCKDOR.G2.A TCP 61466=Telecommando TCP 61603=Bunker-kill TCP 63485=Bunker-kill TCP 65000=Devil, DDoS
TCP 65432=Th3tr41t0r, The Traitor TCP 65530=TROJ_WINMITE.10
TCP 65535=RC,Adore Worm/Linux TCP 69123=ShitHeep
TCP 88798=Armageddon,Hack Office UDP 1=Sockets des Troie UDP 9=Chargen UDP 19=Chargen UDP 69=Pasana UDP 80=Penrox
UDP 371=ClearCase版本管理软件
UDP 445=公共Internet文件系统(CIFS) UDP 500=Internet密钥交换
UDP 1025=Maverick's Matrix 1.2 - 2.0
UDP 1026=Remote Explorer 2000 UDP 1027=HP服务,UC聊天软件,Trojan.Huigezi.e
UDP 1028=应用层网关服务,KiLo,SubSARI UDP 1029=SubSARI UDP 1031=Xot
UDP 1032=Akosch4 UDP 1104=RexxRave UDP 1111=Daodan UDP 1116=Lurker
UDP 1122=Last 2000,Singularity UDP 1183=Cyn,SweetHeart UDP 1200=NoBackO UDP 1201=NoBackO UDP 1342=BLA trojan UDP 1344=Ptakks UDP 1349=BO dll
UDP 1512=Microsoft Windows Internet Name Service
UDP 1561=MuSka52
UDP 1772=NetControle
UDP 1801=Microsoft Message Queue UDP 1978=Slapper
UDP 1985=Black Diver
UDP 2000=A-trojan,Fear,Force,GOTHIC Intruder,Last 2000,Real 2000 UDP 2001=Scalper UDP 2002=Slapper UDP 2015=raid-cs UDP 2018=rellpack
UDP 2130=Mini BackLash
UDP 2140=Deep Throat,Foreplay,The Invasor UDP
2222=SweetHeart,Way,Backdoor/Mifeng.t UDP 2234=DirectPlay UDP 2339=Voice Spy UDP 2702=Black Diver UDP 2989=RAT
UDP 3074=Microsoft Xbox game port UDP 3132=Microsoft Business Rule Engine Update Service UDP 3150=Deep Throat UDP 3215=XHX
UDP 3268=Microsoft Global Catalog UDP 3269=Microsoft Global Catalog with LDAP/SSL
UDP 3333=Daodan
UDP 3535=Microsoft Class Server UDP 3801=Eclypse
UDP 3996=Remote Anything UDP 4128=RedShad UDP 4156=Slapper UDP 4350=Net Device
UDP 4500=Microsoft IPsec NAT-T, sae-urn
UDP 5419=DarkSky
UDP 5503=Remote Shell Trojan UDP 5555=Daodan UDP 5678=Remote Replication Agent Connection
UDP 5679=Direct Cable Connect Manager UDP 5720=Microsoft Licensing UDP 5882=Y3K RAT UDP 5888=Y3K RAT
UDP 6073=DirectPlay8
UDP 6112=Battle. net Game UDP 6666=KiLo UDP 6667=KiLo UDP 6766=KiLo
UDP 6767=KiLo,UandMe
UDP 6838=Mstream Agent-handler UDP 7028=未知木马
UDP 7424=Host Control UDP 7788=Singularity
UDP 7983=MStream handler-agent UDP 8012=Ptakks
UDP 8090=Aphex's Remote Packet Sniffer UDP 8127=9_119,Chonker UDP 8488=KiLo UDP 8489=KiLo
UDP 8787=BackOrifice 2000 UDP 8879=BackOrifice 2000
UDP 9325=MStream Agent-handler UDP 10000=XHX
UDP 10067=Portal of Doom UDP 10084=Syphillis UDP 10100=Slapper
UDP 10167=Portal of Doom UDP 10498=Mstream UDP 10666=Ambush UDP 11225=Cyn
UDP 12321=Protoss
UDP 12345=BlueIce 2000 UDP 12378=W32/Gibe@MM
UDP 12623=ButtMan,DUN Control UDP 11320=IMIP Channels Port
UDP 15210=UDP remote shell backdoor server
UDP 15486=KiLo UDP 16514=KiLo UDP 16515=KiLo
UDP 18753=Shaft handler to Agent UDP 20433=Shaft
UDP 21554=GirlFriend
UDP 22784=Backdoor.Intruzzo UDP 23476=Donald Dick UDP 25123=MOTD
UDP 26274=Delta Source UDP 26374=Sub-7 2.1 UDP 26444=Trin00/TFN2K UDP 26573=Sub-7 2.1
UDP 27184=Alvgus trojan 2000 UDP 27444=Trinoo UDP 29589=KiLo
UDP 29891=The Unexplained UDP 30103=NetSphere UDP 31320=Little Witch
UDP 31335=Trin00 DoS Attack
UDP 31337=Baron Night, BO client, BO2, Bo Facil, BackFire, Back Orifice, DeepBO UDP 31338=Back Orifice, NetSpy DK, DeepBO
UDP 31339=Little Witch UDP 31340=Little Witch UDP 31416=Lithium UDP 31787=Hack aTack UDP 31789=Hack aTack UDP 31790=Hack aTack UDP 31791=Hack aTack UDP 33390=未知木马 UDP 34555=Trinoo UDP 35555=Trinoo UDP 43720=KiLo UDP 44014=Iani
UDP 44767=School Bus UDP 46666=Taskman
UDP 47262=Delta Source
UDP 47624=Direct Play Server UDP 47785=KiLo
UDP 49301=OnLine keyLogger UDP 49683=Fenster UDP 49698=KiLo UDP 52901=Omega
UDP 54320=Back Orifice
UDP 54321=Back Orifice 2000 UDP 54341=NetRaider Trojan UDP 61746=KiLO UDP 61747=KiLO UDP 61748=KiLO
UDP 65432=The Traitor
UDP 31335=Trin00 DoS Attack
UDP 31337=Baron Night, BO client, BO2, Bo Facil, BackFire, Back Orifice, DeepBO UDP 31338=Back Orifice, NetSpy DK, DeepBO
UDP 31339=Little Witch UDP 31340=Little Witch UDP 31416=Lithium UDP 31787=Hack aTack UDP 31789=Hack aTack UDP 31790=Hack aTack UDP 31791=Hack aTack UDP 33390=未知木马 UDP 34555=Trinoo UDP 35555=Trinoo UDP 43720=KiLo UDP 44014=Iani
UDP 44767=School Bus UDP 46666=Taskman
UDP 47262=Delta Source
UDP 47624=Direct Play Server UDP 47785=KiLo
UDP 49301=OnLine keyLogger UDP 49683=Fenster UDP 49698=KiLo
UDP 52901=Omega
UDP 54320=Back Orifice
UDP 54321=Back Orifice 2000 UDP 54341=NetRaider Trojan UDP 61746=KiLO UDP 61747=KiLO UDP 61748=KiLO
UDP 65432=The Traitor
